A hacker is threatening to leak 106GB of data allegedly stolen from Spanish telecommunications company Telef�nica in a breach that the company did not acknowledge.
The threat actor has leaked a 2.6GB archive that unpacks into five gigabytes of data with a little over 20,000 files to prove that the breach occurred.
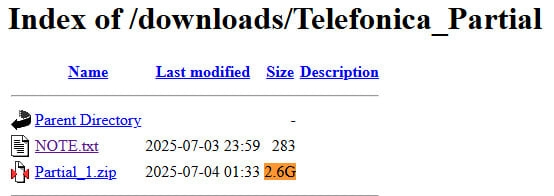 Partial leak with data allegedly stolen from Telef�nica
Partial leak with data allegedly stolen from Telef�nica The breach allegedly occurred on May 30 and the hacker claims they had 12 hours of uninterrupted data exfiltration before defenders revoked access.
The hacker claiming responsibility for the attack is known as "Rey" and is a member of the Hellcat Ransomware group - responsible for another breach at Telef�nica in January through an internal Jira development and ticketing server.
Rey told BleepingComputer that they exfiltrated 385,311 files totaling 106.3GB of internal communications (e.g. tickets, emails), purchase orders, internal logs, customer records, and employee data.
They also said that the May 30 breach was possible because of a Jira misconfiguration after the company dealt with the previous compromise.
BleepingComputer tried on multiple occasions since June 3rd to reach out to Telef�nica over email. We also contacted several C-suite employees but received no acknowledgment of the May 30 breach.
The only response we received came from a Telef�nica O2 employee, who dismissed the alleged incident as an extortion attempt using outdated information from a previously known incident.
Telef�nica O2 is the Spanish companys brand for its telecommunications businesses in the U.K. and Germany.
Rey shared with BleepingComputer a sample and file tree of the data allegedly stolen from Telef�nica on May 30. Some of the files included invoices to business clients in multiple countries, including Hungary, Germany, Spain, Chile, and Peru.
In the files we received there were email addresses for employees in Spain, Germany, Peru, Argentina, and Chile, and invoices for business partners or customers in European countries.
The most recent file we could find in all the info Rey shared was from 2021, though, which seems to confirm what the company representative told us.
However, the hacker is adamant about the data coming from a new breach from May 30. To prove their point, they started leaking a part of the allegedly stolen files.
Since Telefonica has been denying a recent 106 GB breach containing data from its internal infrastructure, I am releasing 5 GB here as proof. Soon, I will publish the full file tree, and over the next few weeks, if Telefonica does not comply, the entire archive will be released. ;) - Rey said.
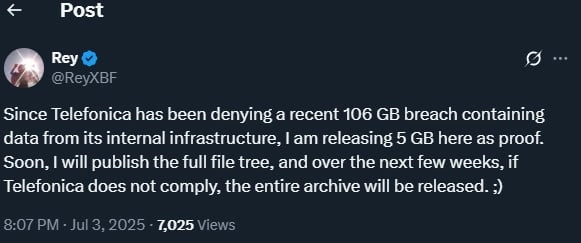 Threat actor announces Telef�nica leak of 106GB
Threat actor announces Telef�nica leak of 106GB The data was initially distributed using the PixelDrain storage and data transfer services but it was removed after a few hours for legal reasons.
The threat actor later distributed another download link from Kotizada, a service then turned to another service, Kotizada, which Google Chrome flags as a dangerous site and strongly recommends users to avoid it.
Until Telef�nica provides an official statement, it is unclear if this is a new breach consisting of old data. However, from BleepingComputer's findings, some of the email addresses in the leak belong to active employees.
The HellCat hacking group is not new on the scene and they are typically focused on targeting Jira servers. They are responsible for multiple attacks at high-profile companies.
They claimed compromises at Swiss global solutions provider Ascom, Jaguar Land Rover, Affinitiv Schneider Electric, and Orange Group.

While cloud attacks may be growing more sophisticated, attackers still succeed with surprisingly simple techniques.
Drawing from Wiz's detections across thousands of organizations, this report reveals 8 key techniques used by cloud-fluent threat actors.